Setup
Setting up Sprinters usually takes around 2 minutes. All you need is a GitHub account and an AWS account.
1. GitHub
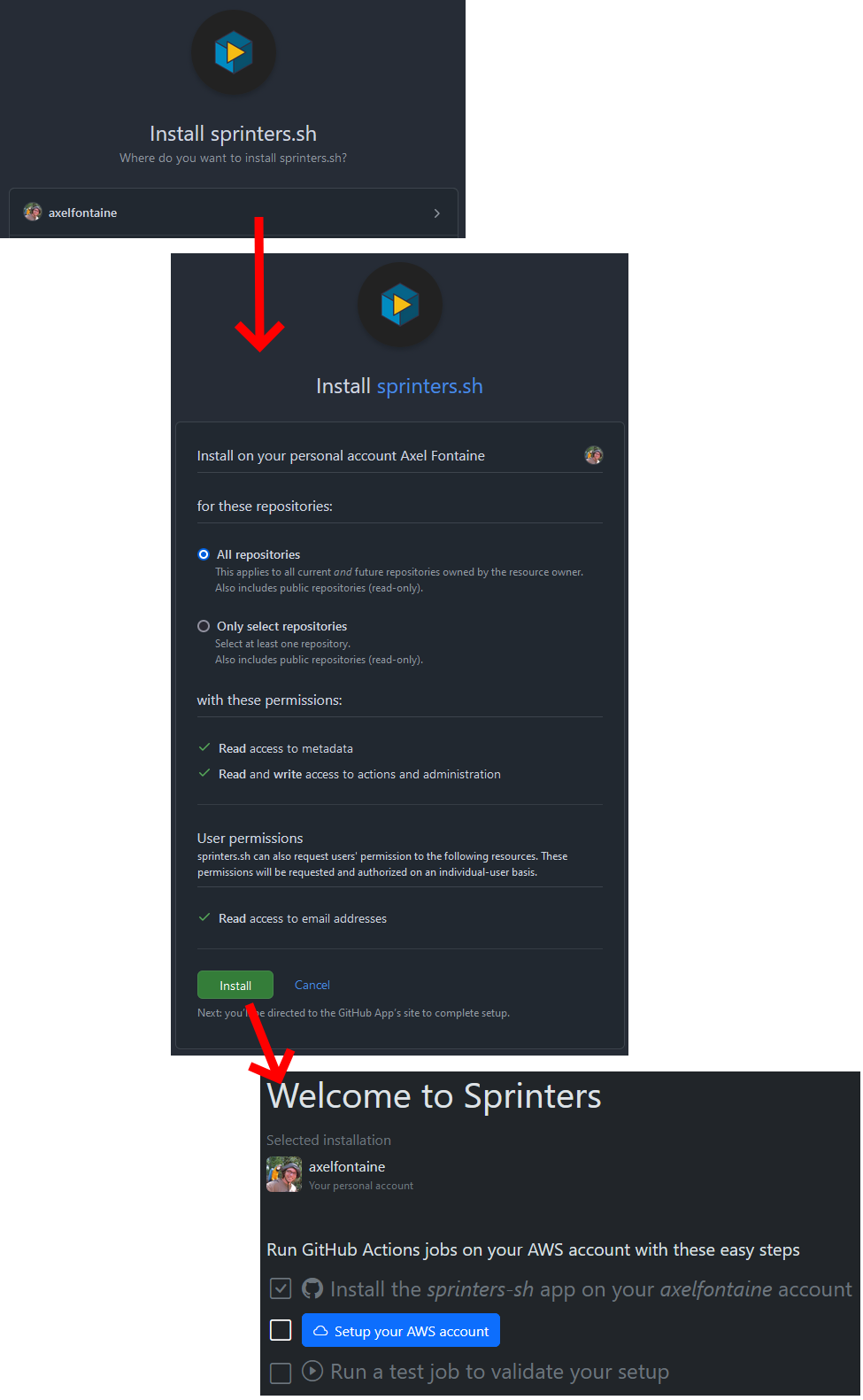
Start by logging in to Sprinters with your GitHub account:
Select your GitHub personal account or organization Sprinters should be installed on and click Install. After a few seconds you will be redirected to Sprinters to set up your AWS account.
Sprinters strictly follows the principle of least-privilege and only requests for the strict minimum set of permissions required to listen to GitHub Actions job events and create runners.
2. AWS
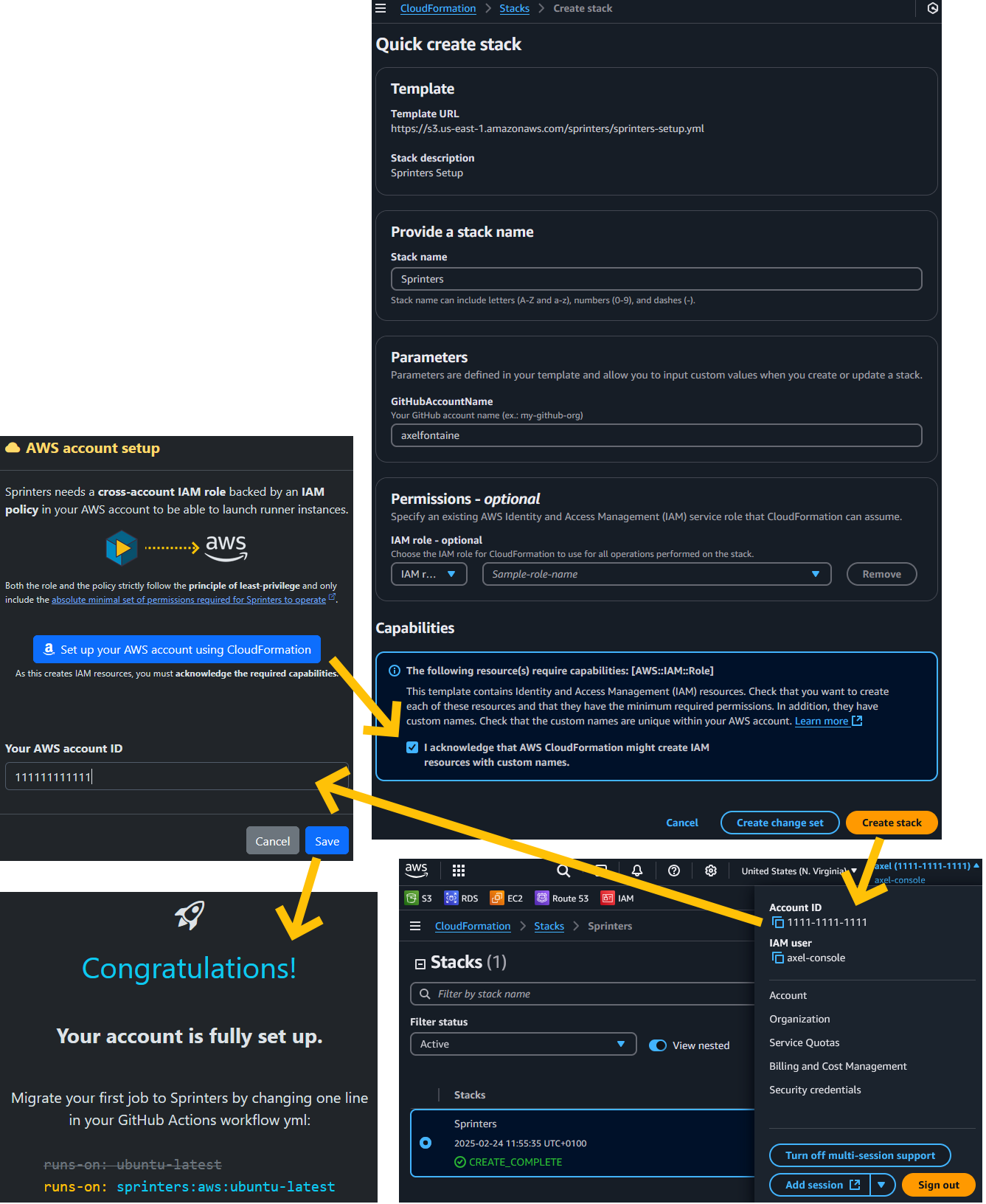
To launch runner instances on your AWS account, Sprinters needs a cross-account IAM role backed by an IAM policy. Setting this up only takes 4 clicks with the Sprinters CloudFormation stack .
Acknowledge the creation of IAM resources and click Create stack. After CloudFormation completes, copy your AWS account ID to complete the setup:
Sprinters strictly follows the principle of least-privilege and the IAM role only grants the strict minimum set of permissions required to launch runner instances.
3. Done
Congratulations! Sprinters is now fully set up!